de_DE
de_DE
For Mikrotik RouterOS 6 we provide some commands for the terminal:
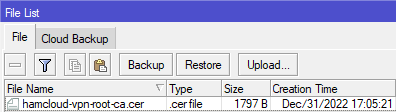
- We need to fetch the HamCloud VPN Server certificate.
/tool fetch url=https://vpn.hc.r1.ampr.org/cert/hamcloud-vpn-root-ca.cer- The HamCloud VPN Server certificate need to show up in the file list.
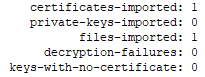
- We need to import the certificate into RouterOS.
/certificate import file-name=hamcloud-vpn-root-ca.cer passphrase=""- RouterOS will report the successful import.
- We need to create an own IPsec proposal with “pfs-group = none”.
/ip ipsec proposal add name=hamcloud-proposal pfs-group=none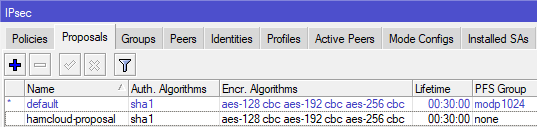
- We need to add this IPsec proposal to an own IPsec policy group.
/ip ipsec policy group add name=hamcloud-policy-group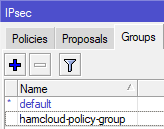
- We need to add an IPsec policy template.
/ip ipsec policy add group=hamcloud-policy-group proposal=hamcloud-proposal template=yes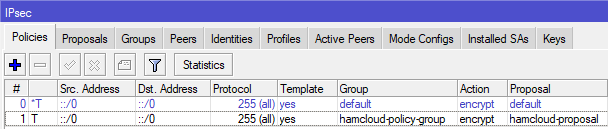
- We need to define the mode.
/ip ipsec mode-config add name=hamcloud-mode-config responder=no use-responder-dns=no connection-mark=no-mark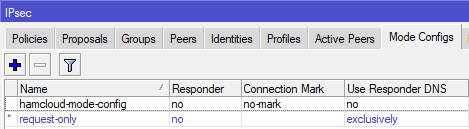
- We need to define the IPsec peer.
/ip ipsec peer add address=[:resolve vpn.hc.r1.ampr.org] exchange-mode=ike2 name=hamcloud-peer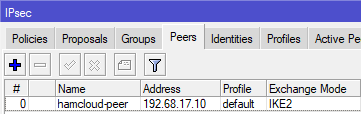
- We need to add an IPsec identity. Exchange “PASSWORD” and “USERNAME” with your IKEv2 HamCloud VPN credentials.
/ip ipsec identity add auth-method=eap certificate="" eap-methods=eap-mschapv2 generate-policy=port-strict mode-config=hamcloud-mode-config password=PASSWORD peer=hamcloud-peer policy-template-group=hamcloud-policy-group username=USERNAME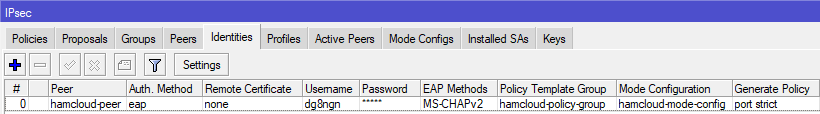
RouterOS 6 will now establish a connection to the HamCloud VPN server:
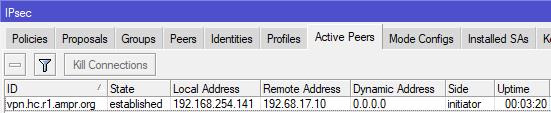
- We can find the active peer.
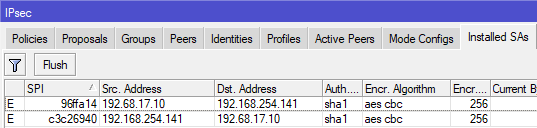
- We can find installed SAs.
- We can find log entries.

- A new IP address from the HamCloud VPN appears.
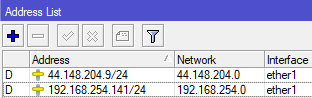
- A new dynamic IPsec policy appears.
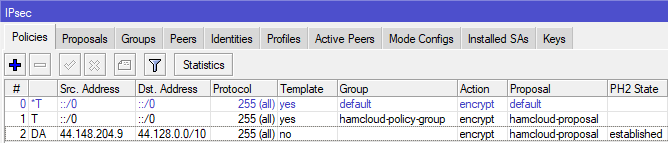
- A new dynamic NAT rule appears.
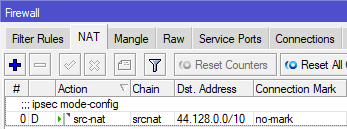
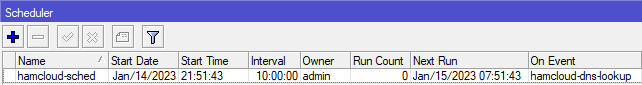
Since the IPsec Peer “vpn.hc.r1.ampr.org” resolves only once to a static IP, we need to run periodically a script to check whether the IP has changed:
- Create the script.
/system script add name=hamcloud-dns-lookup source="{\r\
\n :local newIP ([:resolve vpn.hc.r1.ampr.org] . \"/32\")\r\
\n :local oldIP [/ip ipsec peer get [/ip ipsec peer find name=\"hamcloud-peer\"] address]\r\
\n :if (\$oldIP != \$newIP) do={ /ip ipsec peer set [/ip ipsec peer find name=\"hamcloud-peer\"] address=\$newIP }\r\
\n}\r\
\n"
- Add the script to the scheduler.
/system scheduler add name=hamcloud-sched interval=10h on-event=hamcloud-dns-lookup